Windows 7 Meltdown Patch Download
Home Desktop The impact of Meltdown and Spectre patches on Windows 7. Is affected by the Meltdown and Spectre patches delivered by Microsoft. The Microsoft windows update has a very. Microsoft rolled out Meltdown and Spectre vulnerability patches in January for all supported Windows versions, including Windows 7, and even though further mitigations landed shortly after that, it looks like the original fix opened the door for a different kind of exploits. Direct download links for Windows 7 KB4100480 is available from Microsoft’s official website and this update finally addresses a vulnerability introduced by Meltdown patch released earlier this. Mar 28, 2018 Security researcher Ulf Frisk announced that Microsoft's patch for Meltdown on 64-bit versions of Windows 7 and Windows Server 2008 R2 caused an. Microsoft has released a patch for Windows 7 (and other OS) that fixes the most serious of the two vulnerabilities. However, this patch is only made available to Antivirus 'partners' that have confirmed that their software does not cause issues after the patch is installed.
Warning: Even if you’ve installed patches from Windows Update, your PC may not completely protected from the Meltdown and Spectre CPU flaws. Here’s how to check if you’re fully protected, and what to do if you aren’t.
RELATED:How Will the Meltdown and Spectre Flaws Affect My PC?
To fully protect against Meltdown and Spectre, you’ll need to install a UEFI or BIOS update from your PC’s manufacturer as well as the various software patches. These UEFI updates contain new Intel or AMD processor microcode that adds additional protection against these attacks. Unfortunately, they aren’t distributed via Windows Update—unless you’re using a Microsoft Surface device—so they must be downloaded from your manufacturer’s website and installed manually.
Update: On January 22, Intel announced that users should stop deploying the initial UEFI firmware updates due to “higher than expected reboots and other unpredictable system behavior”. Intel said you should wait for a final UEFI firmware patch. As of February 20, Intel has released stable microcode updates for Skylake, Kaby Lake, and Coffee Lake—that’s the 6th, 7th, and 8th Generation Intel Core platforms. PC manufacturers should begin rolling out new UEFI firmware updates soon.
If you did install a UEFI firmware update from your manufacturer, you can download a patch from Microsoft to make your PC stable again. Available as KB4078130, this patch disables the protection against Spectre Variant 2 in Windows, which prevents the buggy UEFI update from causing system problems. You only need to install this patch if you’ve installed a buggy UEFI update from your manufacturer, and it isn’t being automatically offered via Windows Update. Microsoft will re-enable this protection in the future when Intel releases stable microcode updates.
The Easy Method (Windows): Download the InSpectre Tool
To check whether you’re fully protected, download the Gibson Research Corporation’s InSpectre tool and run it. It’s an easy-to-use graphical tool that will show you this information without the hassle of running PowerShell commands and decoding the technical output.
Once you’ve run this tool, you’ll see a few important details:
- Vulnerable to Meltdown: If this says “YES!”, you’ll need to install the patch from Windows Update to protect your computer from Meltdown and Spectre attacks.
- Vulnerable to Spectre: If this says “YES!”, you’ll need to install the UEFI firmware or BIOS update from your PC’s manufacturer to protect your computer from certain Spectre attacks.
- Performance: If this says anything other than “GOOD”, you have an older PC that doesn’t have the hardware that makes the patches perform well. You’ll likely see a noticeable slowdown, according to Microsoft. If you’re using Windows 7 or 8, you can speed things up some by upgrading to Windows 10, but you’ll need new hardware for maximum performance.
You can see a human-readable explanation of exactly what’s going on with your PC by scrolling down. For example, in the screenshots here, we’ve installed the Windows operating system patch but not a UEFI or BIOS firmware update on this PC. It’s protected against Meltdown, but needs the UEFI or BIOS (hardware) update to be fully protected against Spectre.
The Command Line Method (Windows): Run Microsoft’s PowerShell Script
Microsoft has made available a PowerShell script that will quickly tell you whether your PC is protected or not. Running it will require the command line, but the process is easy to follow. Thankfully, Gibson Research Corporation now provides the graphical utility Microsoft should have, so you don’t have to do this anymore.
If you’re using Windows 7, you will first need to download the Windows Management Framework 5.0 software, which will install a newer version of PowerShell on your system. The script below won’t run properly without it. If you’re using Windows 10, you already have the latest version of PowerShell installed.
On Windows 10, right-click the Start button and select “Windows PowerShell (Admin)”. On Windows 7 or 8.1, search the Start menu for “PowerShell”, right-click the “Windows PowerShell” shortcut, and select “Run as Administrator”.
Type the following command into the PowerShell prompt and press Enter to install the script on your system
If you’re prompted to install the NuGet provider, type “y” and press Enter. You may also have to type “y” again and press Enter to trust the software repository.
The standard execution policy will not allow you to run this script. So, to run the script, you will first save the current settings so you can restore them later. Then you’ll change the execution policy so the script can run. Run the following two commands to do this:
Type “y” and press Enter when you’re asked to confirm.
Then, to actually run the script, run the following commands:
You will see information about whether your PC has the appropriate hardware support. In particular, you’ll want to look for two things:
- The “Windows OS support for branch target injection mitigation” refers to the software update from Microsoft. You’ll want this to be present to protect against both Meltdown and Spectre attacks.
- The “hardware support for branch target injection mitigation” refers to the UEFI firmware/BIOS update that you’ll need from your PC manufacturer. You’ll want this to be present to protect against certain Spectre attacks.
- The “Hardware requires kernel VA shadowing” will show as “True” on Intel hardware, which is vulnerable to Meltdown, and “False” on AMD hardware, which isn’t vulnerable to Meltdown. Even if you have Intel hardware, you’re protected as long as the operating system patch is installed and “Windows OS support for kernel VA shadow is enabled” reads “True”.
So in the screenshot below, the command tells me that I have the Windows patch, but not the UEFI/BIOS update.
This command also shows whether your CPU has the “PCID performance optimization” hardware feature that makes the fix perform more speedily here. Intel Haswell and later CPUs have this feature, while older Intel CPUs don’t have this hardware support and may see more of a performance hit after installing these patches.
To reset the execution policy to its original settings after you’re done, run the following command:
Type “y” and press Enter when prompted to confirm.
How to Get the Windows Update Patch for Your PC
If “Windows OS support for branch target injection mitigation is present” is false, that means your PC hasn’t yet installed the operating system update that protects against these attacks.
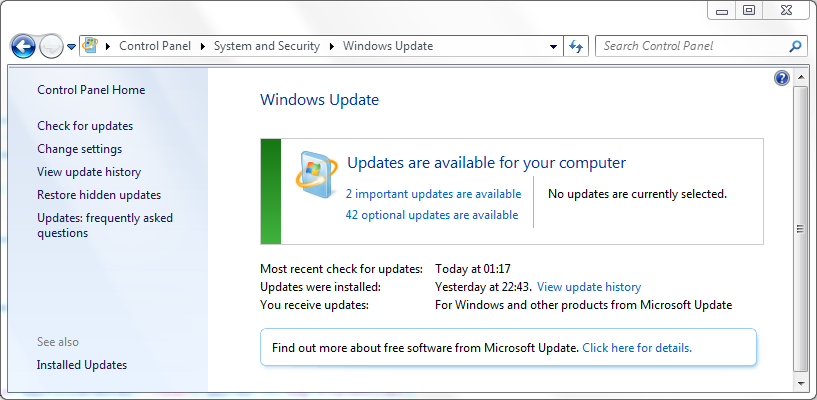
To get the patch on Windows 10, head to Settings > Update & security > Windows Update and click “Check for updates” to install any available updates. On Windows 7, head to Control Panel > System and Security > Windows Update and click “Check for updates”.
If no updates are found, your antivirus software may be causing the problem, as Windows won’t install it if your antivirus software isn’t yet compatible. Contact your antivirus software provider and ask for more information about when their software will be compatible with the Meltdown and Spectre patch in Windows. This spreadsheet shows which antivirus software has been updated for compatibility with the patch.
Other Devices: iOS, Android, Mac, and Linux
Patches are now available to protect against Meltdown and Spectre on a wide variety of devices. It’s unclear if game consoles, streaming boxes, and other specialized devices are affected, but we know that the Xbox One and Raspberry Pi are not. As always, we recommend keeping up-to-date with security patches on all your devices. Here’s how to check if you already have the patch for other popular operating systems:
- iPhones and iPads: Head to Settings > General > Software Update to check the current version of iOS you have installed. If you have at least iOS 11.2, you are protected against Meltdown and Spectre. If you don’t, install any available updates that appear on this screen.
- Android Devices: Head to Settings > About Phone or About Tablet and look at the “Android security patch level” field. If you have at least the January 5, 2018 security patch, you are protected. If you don’t, tap the “System updates” option on this screen to check for and install any available updates. Not all devices will be updated, so contact your manufacturer or check their support documents for more information about when and whether patches will be available for your device.
- Macs: Click the Apple menu at the top of your screen and select “About This Mac” to see what operating system version you have installed. If you have at least macOS 10.13.2, you are protected. If you don’t, launch the App Store and install any available updates.
- Chromebooks: This Google support document shows which Chromebooks are vulnerable to Meltdown, and whether they’ve been patched. Your Chrome OS device is always checking for updates, but you can manually initiate an update by heading to Settings > About Chrome OS > Check for and apply updates.
- Linux Systems: You can run this script to check whether you’re protected against Meltdown and Spectre. Run the following commands in a Linux terminal to download and run the script:
Linux kernel developers are still working on patches that will fully protect against Spectre. Consult your Linux distribution for more information about patch availability.
Windows and Linux users will need to take one more step, however, to secure their devices.
Windows and Linux: How to Get the UEFI/BIOS Update for Your PC
If “hardware support for branch target injection mitigation” is false, you’ll need to get the UEFI firmware or BIOS update from your PC’s manufacturer. So if you have a Dell PC, for example, head to Dell’s support page for your model. If you have a Lenovo PC, head to Lenovo’s web site and search for your model. If you built your own PC, check your motherboard manufacturer’s website for an update.
Once you’ve found the support page for your PC, head to the Driver Downloads section and look for any new versions of the UEFI firmware or BIOS. If your machine has an Intel processor in it, you need a firmware update that contains the “December/January 2018 microcode” from Intel. But even systems with an AMD processor need an update. If you don’t see one, check back in the future for your PC’s update if it isn’t yet available. Manufacturers need to issue a separate update for each PC model they’ve released, so these updates may take some time.
RELATED:How to Check Your BIOS Version and Update it
Once you’ve downloaded the update, follow the instructions in the readme to install it. Usually this will involve putting the update file on a flash drive, then launching the update process from your UEFI or BIOS interface, but the process will vary from PC to PC.
Intel says it will release updates for 90% of processors released in the last five years by January 12, 2018. AMD is already releasing updates. But, after Intel and AMD have released those processor microcode updates, manufacturers will still need to package them up and distribute them to you. It’s unclear what will happen with older CPUs.
After you’ve installed the update, you can double-check and see whether the fix is enabled by running the installed script again. It should show “Hardware support for branch target injection mitigation” as “true”.
You Also Need to Patch Your Browser (and Maybe Other Applications)
The Windows update and BIOS update aren’t the only two updates you need. You’ll also need to patch your web browser, for example. If you use Microsoft Edge or Internet Explorer, the patch is included in the Windows Update. For Google Chrome and Mozilla Firefox, you’ll need to ensure you have the latest version—these browsers automatically update themselves unless you’ve gone out of your way to change that, so most users won’t have to do much. Initial fixes are available in Firefox 57.0.4, which has already been released. Google Chrome will receive patches starting with Chrome 64, which is scheduled for release on January 23, 2018.
RELATED:How to Keep Your Windows PC and Apps Up to Date
Windows 7 Meltdown Patch Download Download
Browsers aren’t the only piece of software that needs to be updated. Some hardware drivers may be vulnerable to Spectre attacks and need updates as well. Any application that interprets untrusted code—like how web browsers interpret JavaScript code on web pages—needs an update to protect against Spectre attacks. This is just one more good reason to keep all your software up to date, all the time.
Image Credit: Virgiliu Obada/Shutterstock.com and cheyennezj/Shutterstock.com
READ NEXT- › How to Get Help in Windows 10
- › How to Enable Ultra-Low Latency Mode for NVIDIA Graphics
- › The New Microsoft Edge Is Now “Ready for Everyday Use”
- › Can You Use iMessage on a Windows PC or Android Phone?
- › What Is VBScript, and Why Did Microsoft Just Kill It?
A critical flaw was found in all Intel processors launched in the past decade. The vulnerability can allow an attacker to gain access to protected kernel memory. This chip-level security flaw cannot be fixed with a CPU microcode (software) update. Instead, it requires modification of the OS kernel. Earlier today, Microsoft released security patches for Windows 10. The appropriate patches are now available for Windows 7 and Windows 8.1.
RECOMMENDED: Click here to fix Windows errors and optimize system performance
Here are some details.
Meltdown and Spectre exploit critical vulnerabilities in modern processors. These hardware bugs allow programs to steal data which is currently processed on the computer. While programs are typically not permitted to read data from other programs, a malicious program can exploit Meltdown and Spectre to get hold of secrets stored in the memory of other running programs. This might include your passwords stored in a password manager or browser, your personal photos, emails, instant messages and even business-critical documents.
Meltdown and Spectre work on personal computers, mobile devices, and in the cloud. Depending on the cloud provider's infrastructure, it might be possible to steal data from other customers.
Meltdown breaks the most fundamental isolation between user applications and the operating system. This attack allows a program to access the memory, and thus also the secrets, of other programs and the operating system.
Spectre breaks the isolation between different applications. It allows an attacker to trick error-free programs, which follow best practices, into leaking their secrets. In fact, the safety checks of said best practices actually increase the attack surface and may make applications more susceptible to Spectre. Spectre is harder to exploit than Meltdown, but it is also harder to mitigate.
Refer to these web sites:
- https://spectreattack.com/
- https://meltdownattack.com/
Patches have already been released for Windows 10, Linux and macOS. Now, the same updates are available for Windows 7 and Windows 8.1.
Download CPU flaw fixes
Microsoft Windows 7 Meltdown Patch Kb#
- KB4056898 for Windows 8.1
- KB4056897 for Windows 7 SP1
Also, the updates can be downloaded from the Windows Update catalog.
- Windows 8.1
- Windows 7 SP1
An unfortunate consequence of this security vulnerability is that its patches are expected to slow down all devices anywhere between 5 to 30 percent depending on the processor and software being used. Even ARM and AMD CPUs may get performance degradation due to fundamental changes in how the OS kernel works with memory. According to Intel, processors with PCID / ASID (Skylake or newer) will have less performance degradation.
RECOMMENDED: Click here to fix Windows errors and optimize system performance